2-6 weeks
Time to first protected workflow
Launch with one critical vendor path, validate controls, then replicate by template.
Autonomous Secure Access for OT/ICS
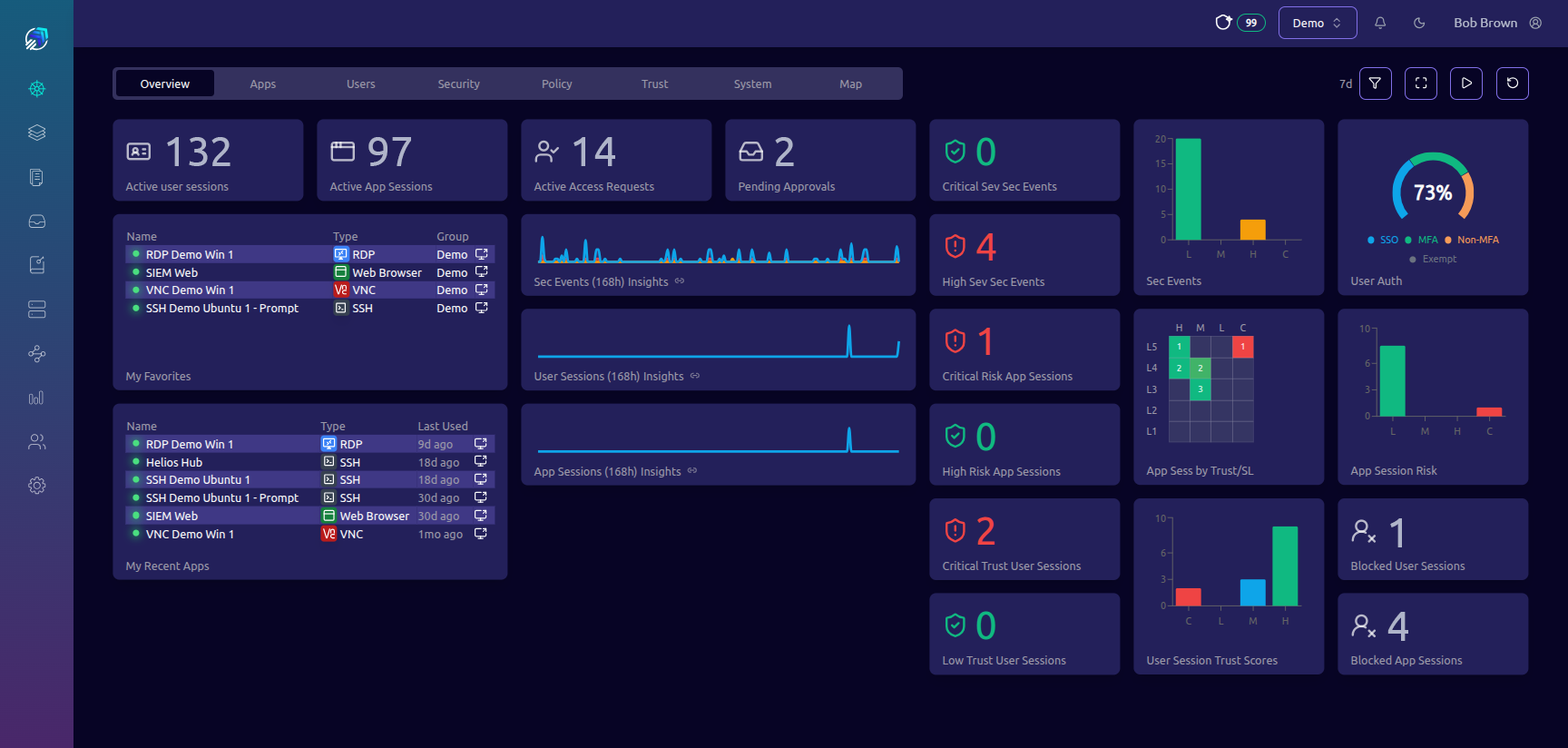
Most tools authenticate once, then lose control of live sessions. Hyperport continuously scores risk and enforces policy in-session so threats are contained before they become incidents.
Step-up auth, privilege reduction, pause, or revoke.
Continuous scoring across the session, not just at login.
Identity, device, behavior, OT context, network, and asset criticality.
In critical infrastructure, risk changes minute-by-minute while sessions stay open for vendors and operators. If controls cannot adapt live, security inherits blind spots and operations inherit exposure.
Hyperport turns identity, posture, behavior, and asset context into live policy decisions. Enforcement keeps pace with the session while preserving operational continuity and auditability.
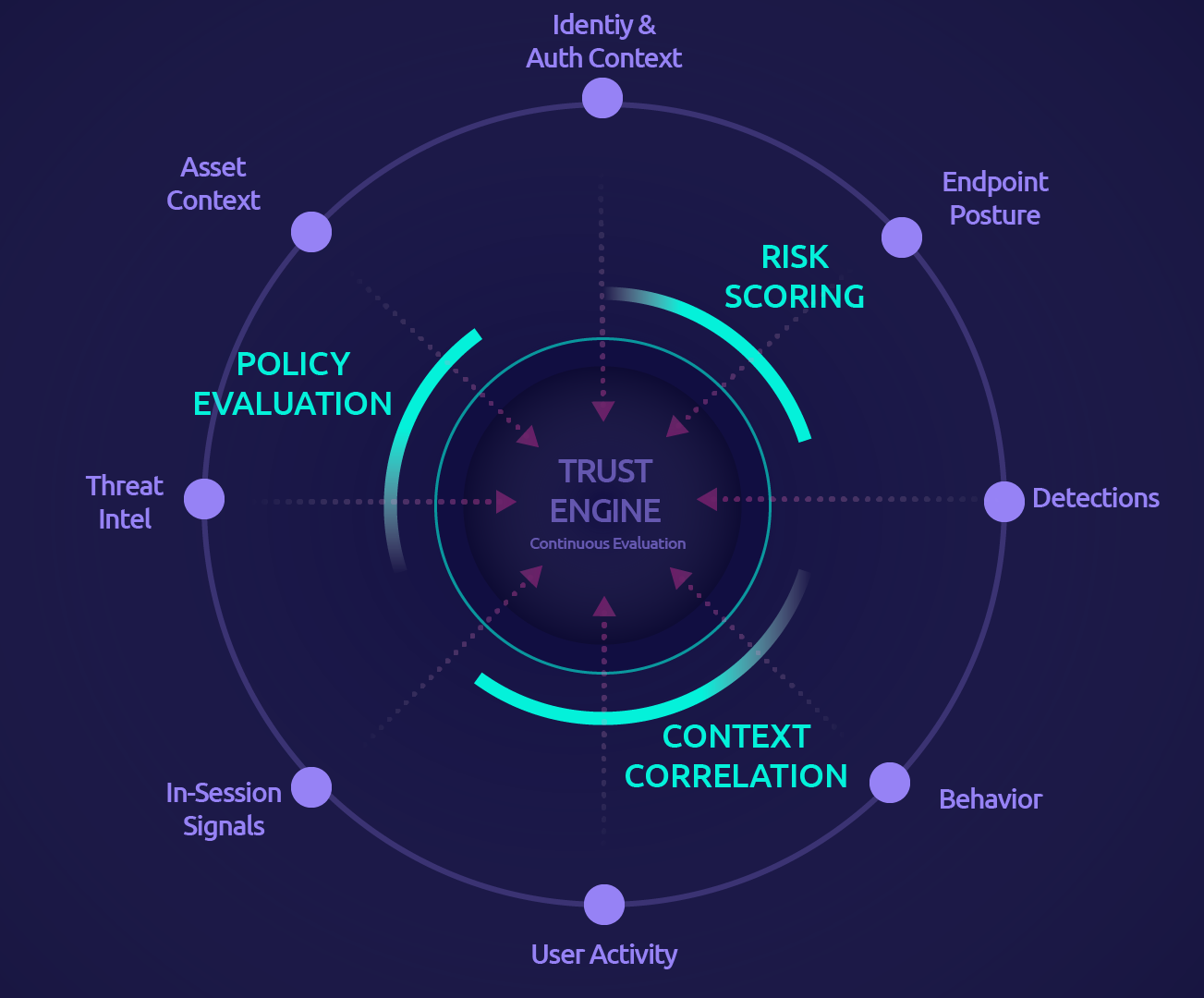
Live risk scores update throughout every session, not just at login.
Policies trigger step-up auth, privilege reduction, or pause actions immediately.
Automation stays inside guardrails security and operations teams define together.
Directional ranges teams use for business cases and pilot scoping. These are planning inputs.
2-6 weeks
Launch with one critical vendor path, validate controls, then replicate by template.
20-40%
Live trust updates reduce ticket churn, exception handling, and reactive escalations.
30-60%
Session controls, recordings, and logs improve readiness for internal and external audits.
Give users fast access while security keeps session-level control and compliance keeps clean evidence.
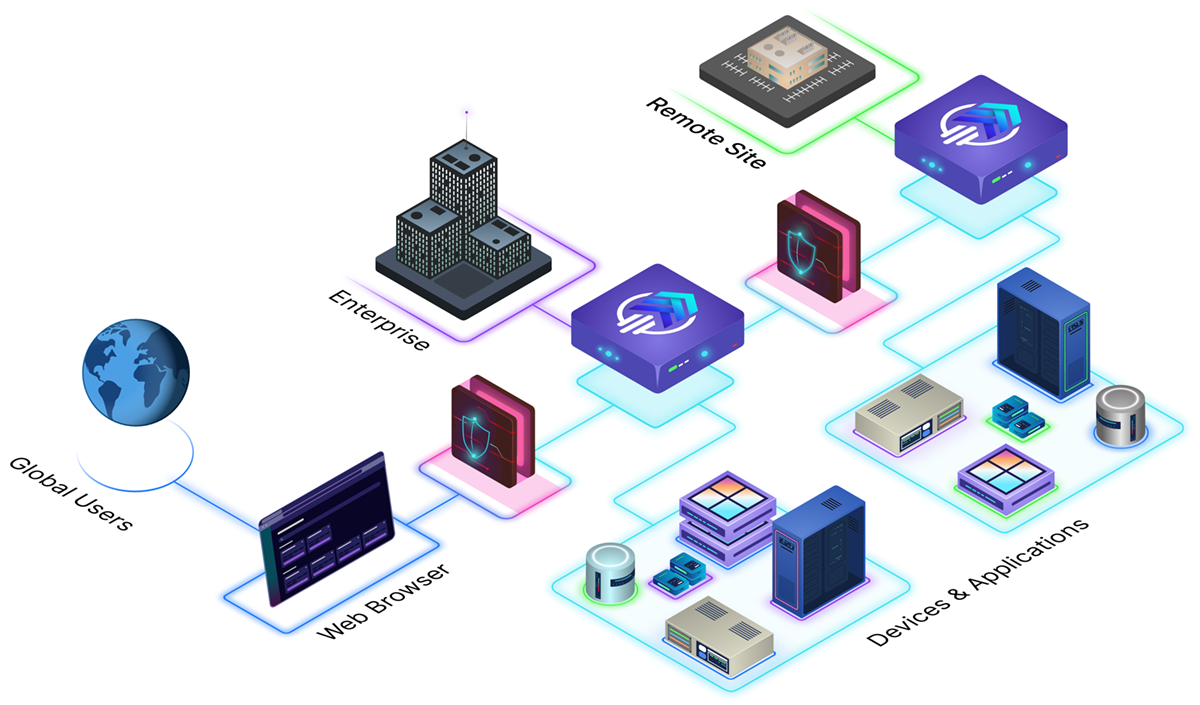
Hyperport unifies access to apps, devices, and data in one control plane. From first login through session completion, teams can observe, control, and audit every action while keeping operators and vendors productive.
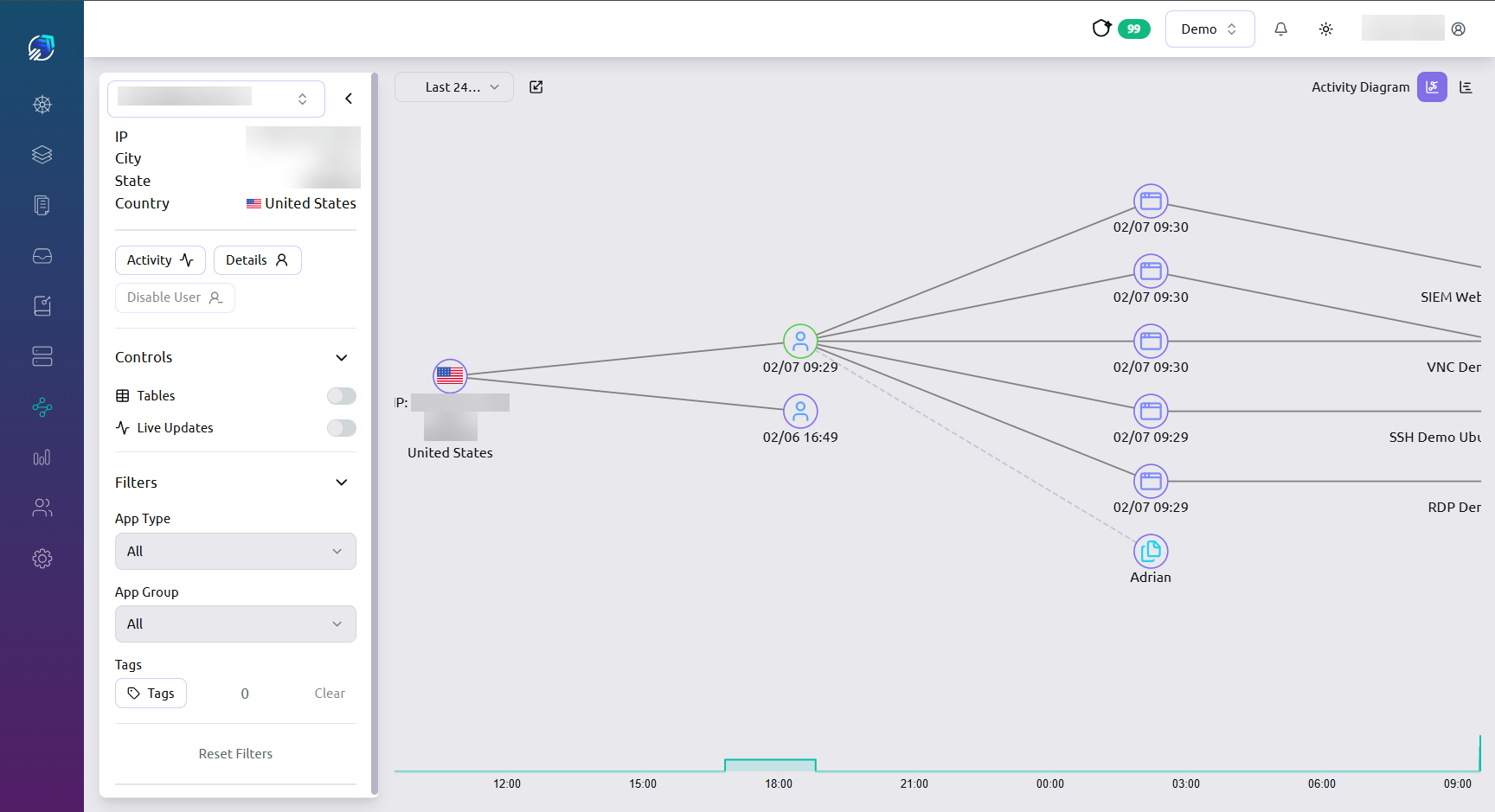
Start with one high-risk workflow, prove value quickly, then expand by repeating what works. Hyperport supports phased adoption without disruptive architecture resets.
The platform supports on-prem, cloud, hybrid, and air-gapped environments with multi-appliance architecture, IPSec tunnels, and active-active high availability. Scale your secure access program at your pace while keeping operations stable and continuously governed.
Power utilities, oil and gas, data centers, and any operation where uptime is mandatory.

Secure vendor access across generation, transmission, and distribution.

Govern third-party access to upstream, midstream, and downstream assets.

Control privileged access with continuous trust and zero disruption.

Manufacturing, transportation, water, and regulated facilities.
Every session is governed, recorded, and logged with policy enforcement that remains consistent across users, systems, and sites. Hyperport gives security and compliance teams continuous visibility into access behavior while preserving the operational speed OT environments require.
From day-to-day controls to formal audits, teams can produce clear, defensible evidence for regulated frameworks without stitching together disconnected tools or interrupting critical work.
Security Leadership
OT / SOC Teams
Compliance & Governance
Built by experienced operators in cybersecurity, OT, and critical infrastructure.

Founder & CEO

Founder & CTO

VP of Sales

AVP & Advisor

Advisor, Former FBI, NRO & DoD

Senior Executive & Advisor
Three select resources for OT/ICS security leaders. Full library on the Resources page.

Hyperport introduces ASA and the v3.3 Trust Engine update.
Read release
Core capabilities, deployment options, and secure access controls.
View datasheet
Hyperport expands to APAC through a regional distribution partnership.
Read releaseMost teams start with one external user workflow in one site, then standardize policy templates and scale to additional plants or regions.
We will map one high-impact workflow, define a phased plan, and align enforcement to your risk and compliance priorities.